
Security Means Freedom
Aqua unleashes the power of cloud native security so your business and applications can run free.
Aqua Security enables enterprises to secure their container-based and cloud-native applications from development to production, accelerating container adoption and bridging the gap between DevOps and IT security.
Aqua’s Container Security Platform provides full visibility into container activity, allowing organizations to detect and prevent suspicious activity and attacks, providing transparent, automated security while helping to enforce policy and simplify regulatory compliance.
Full Lifecycle Container Security
Protect container-based cloud native applications from development to production, using the industry’s most advanced container security solution.
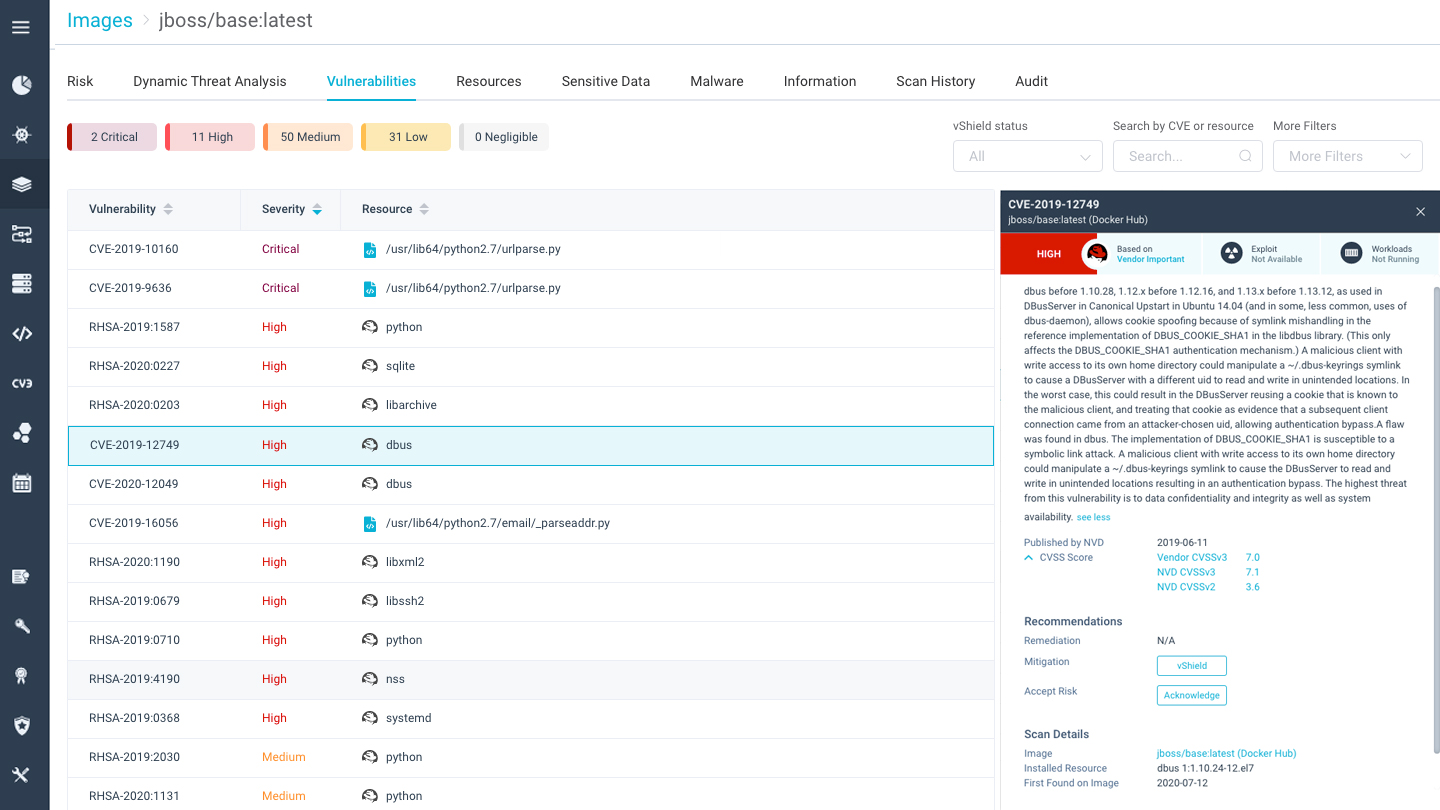
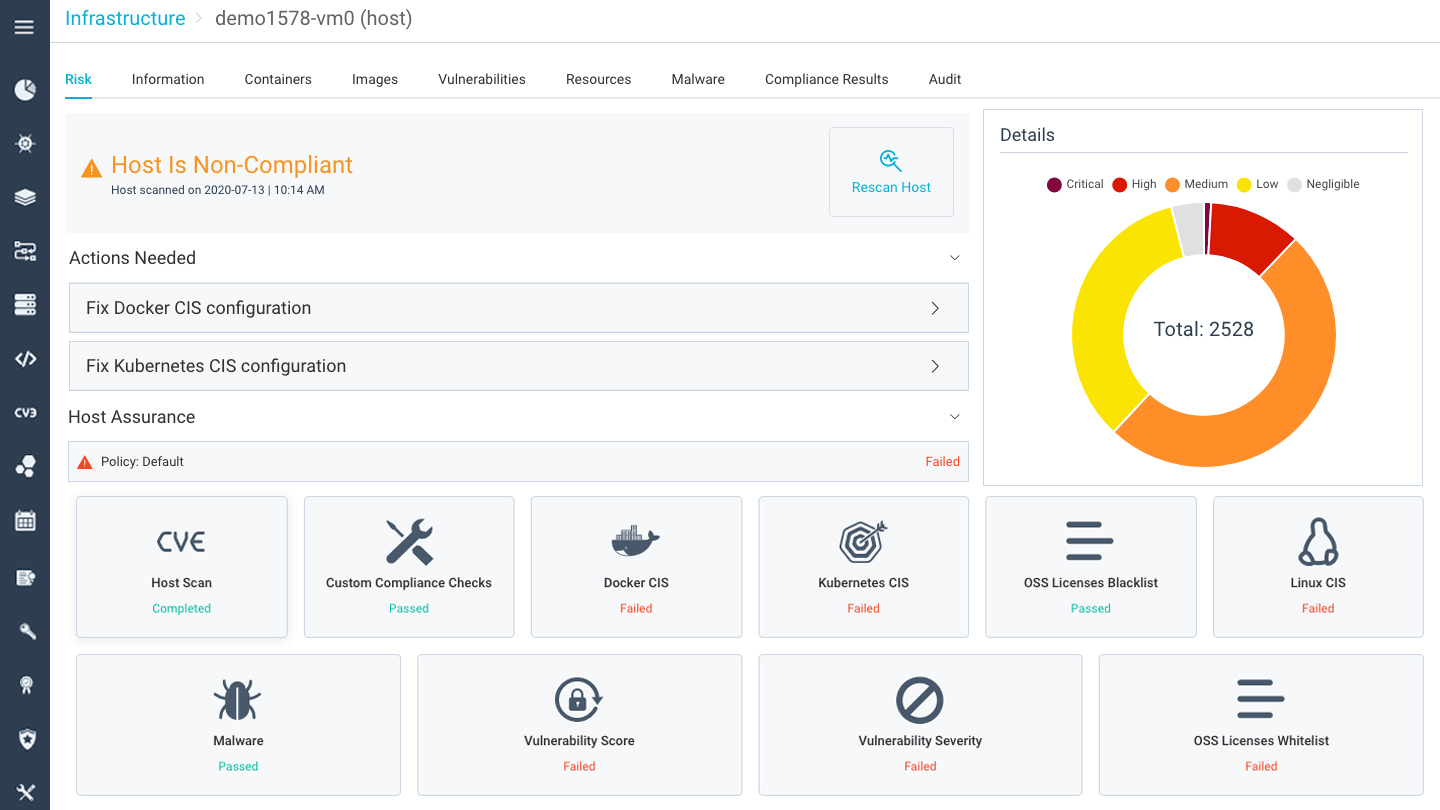
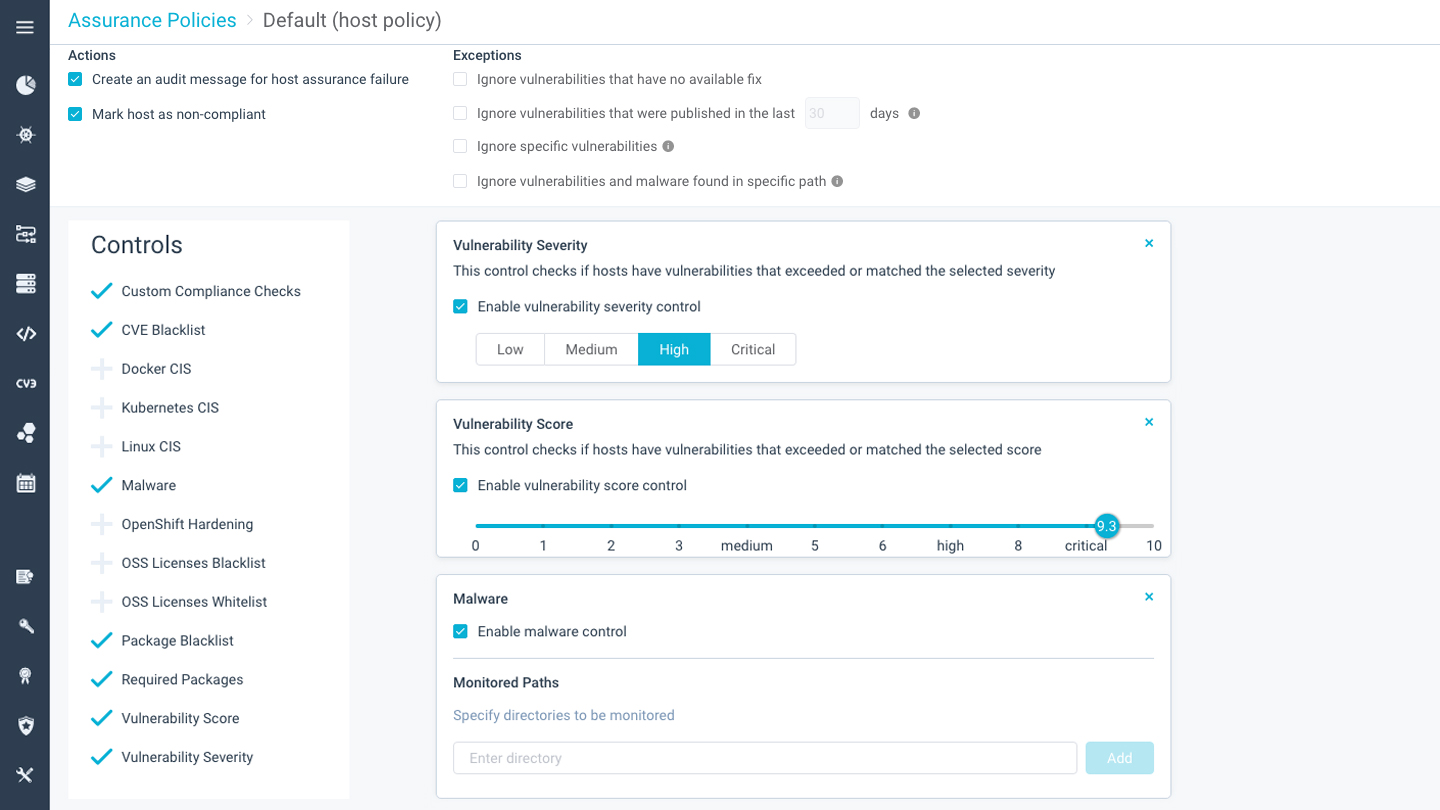
Reduce Risk and Prove Compliance of Containerized Applications
Gain constant visibility into vulnerability posture in your pipeline, reducing the attack surface before containers are deployed. The get detailed auditing and forensics data of your container and Kubernetes runtime environment to track violation events and compliance posture.
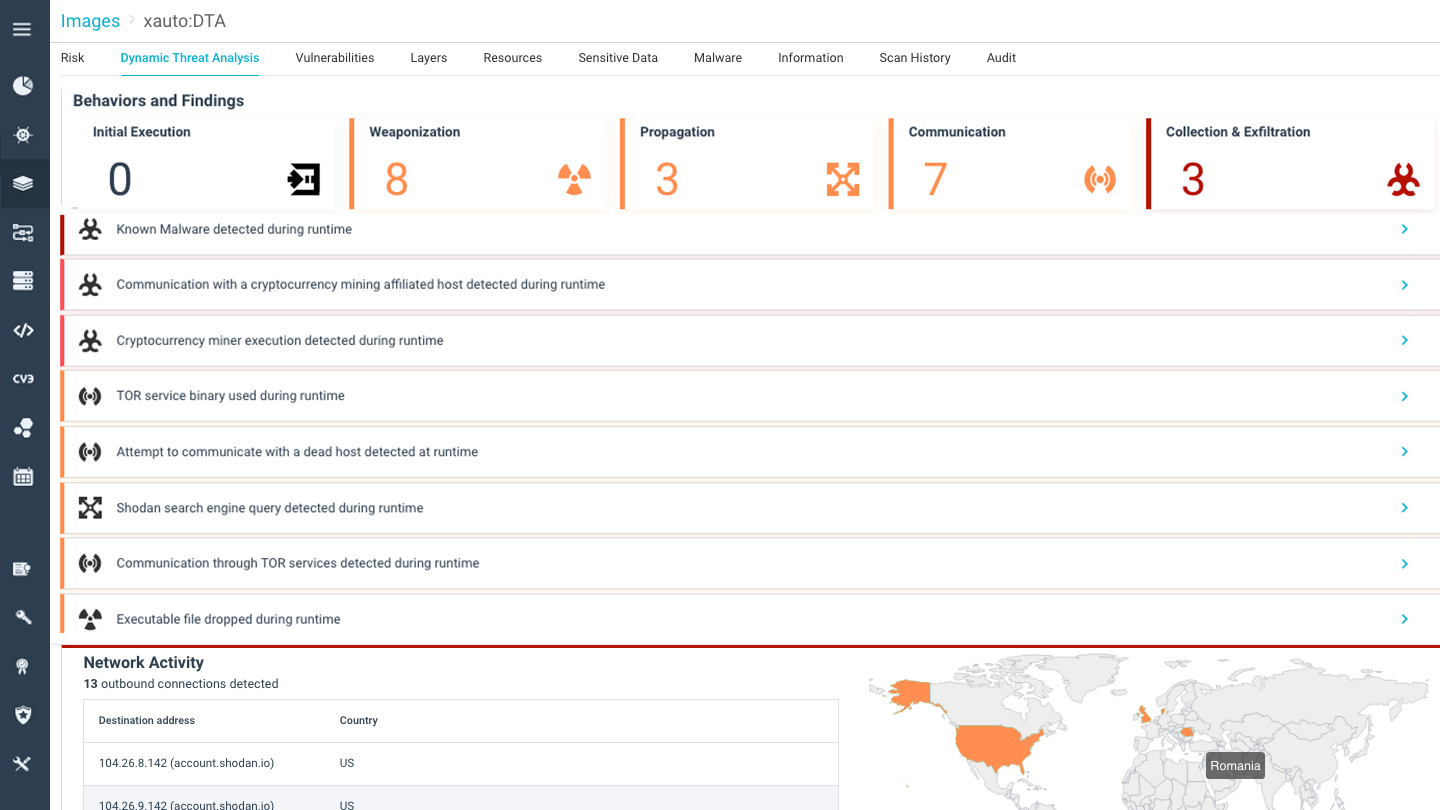
Mitigate Supply Chain and Zero-Day Attacks
Get granular, automated response based on Indicators of Compromise, drift prevention and behavioral profiling to stop malicious behavior, blocking only activities that violate policy with no impact on legitimate container operation.
Protect Containers Across All Platforms and Formats
Secure Linux and Windows containers, and protect containers running on VM, bare-metal, on Container-as-a-Service offerings such as AWS Fargate and ACI, even on Tanzu Application Service. Aqua has purpose-built runtime instrumentation (the Aqua Enforcer family) for each of these environments.
|  |
 |
|
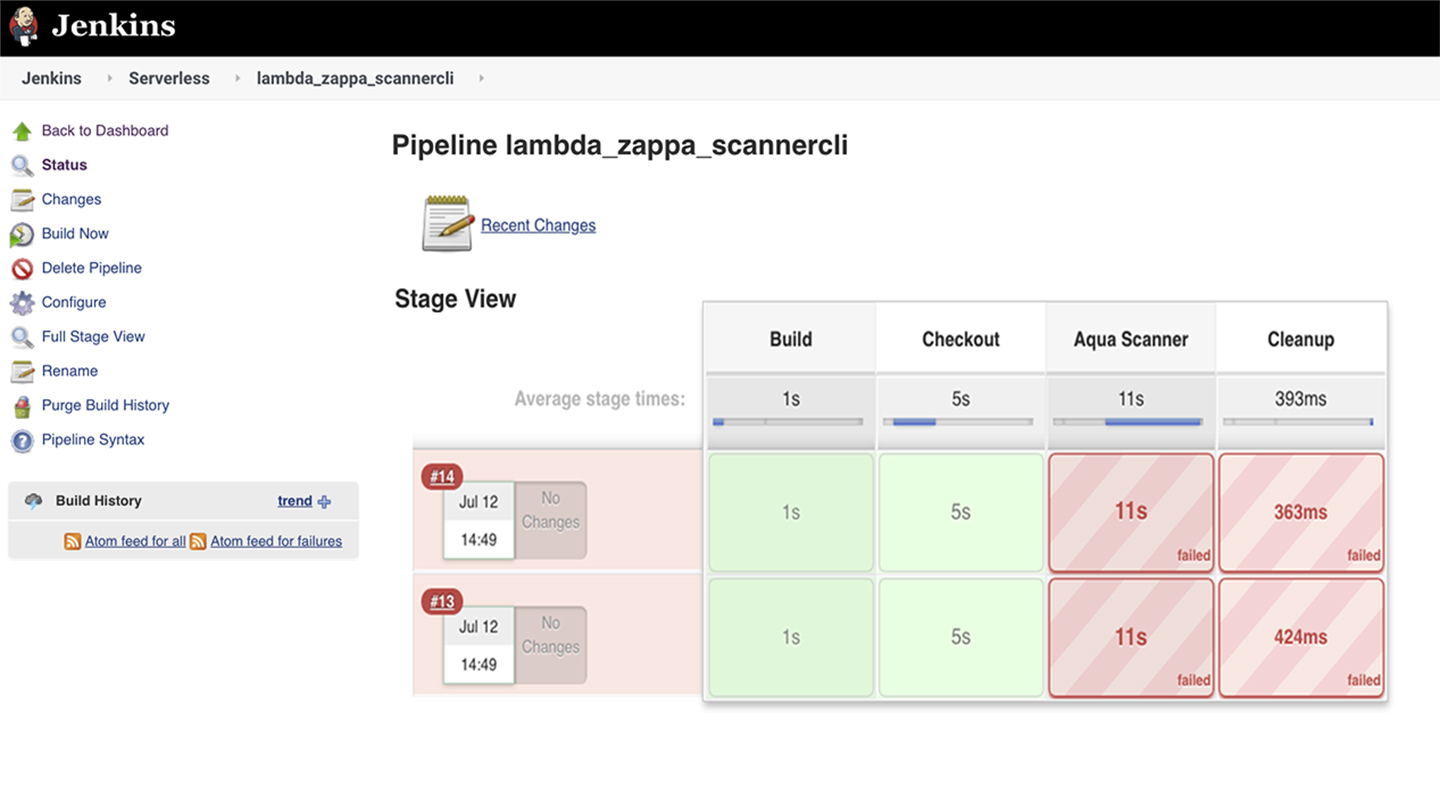
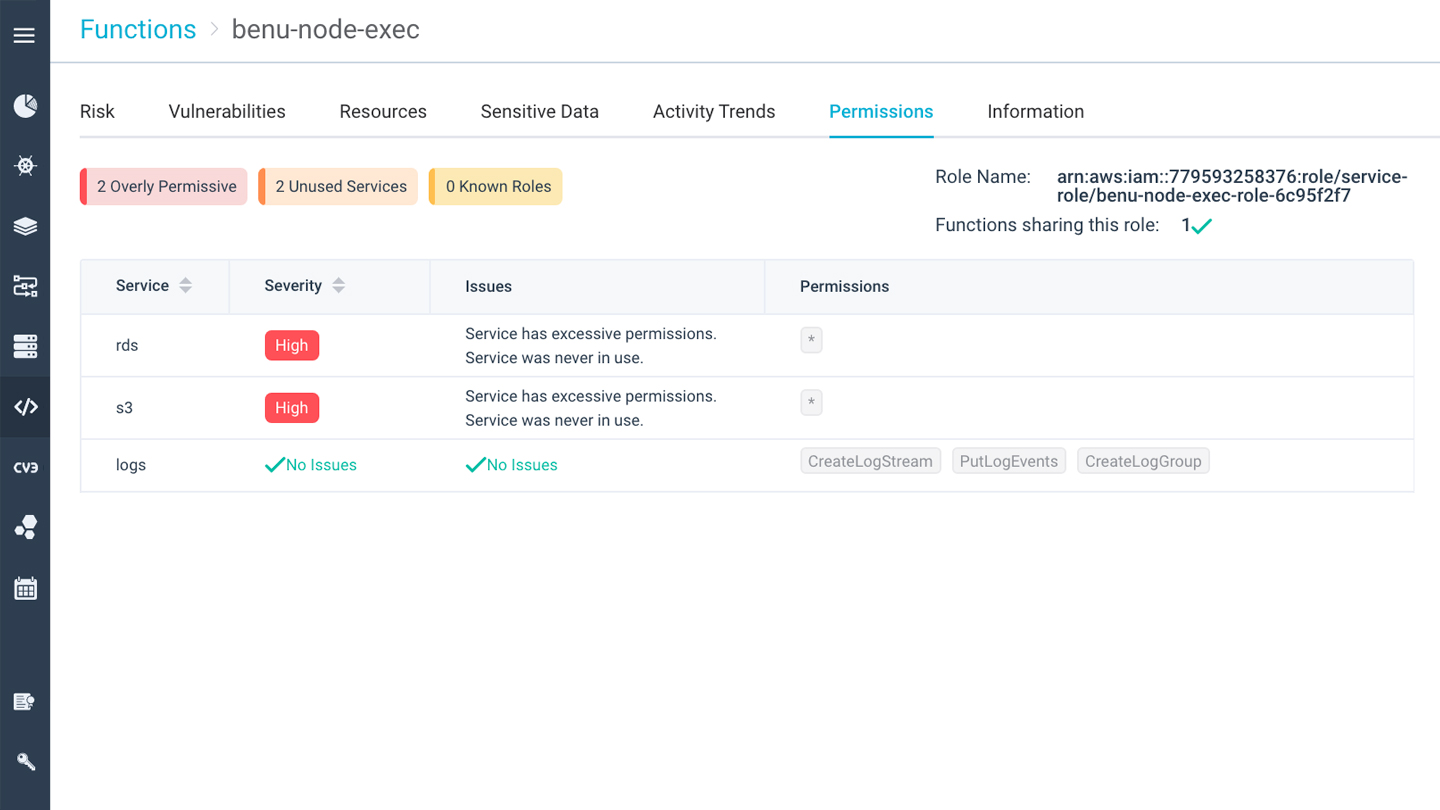
Security for Serverless Functions (FaaS)
Ensure that serverless functions are secured and in compliance. Reduce the attack surface, control deployment, and protect functions in runtime using performance-optimized controls.
|  |
 |
|
Protecting Cloud VMs and Instances
Automate VM security in private, public & hybrid cloud environments. Ensure compliance with PCI-DSS, HIPAA and other requirements, detect configuration issues quickly, and protect VM-based workloads in runtime.
Prevent intrusions and safeguard data
Use real-time controls to detect suspicious activity on cloud VMs such as Amazon EC2 instances. Monitor files and folders for read, write, and attribute changes.
|  |
 |
|
